Authentication Protocol or Authentication Method is one of the hidden and unattended topics. Most of us have faced scripting challenges mostly in correlating the dynamic values. If the correlated script is passed in one go then we just proceed ahead without thinking about the type of authentication, but in case we stuck then it is difficult to get out of the mud. The complex nature of dynamic values is associated with the kind of authentication protocols employed in the application.
This article will help you understand the different types of authentication protocols, their features, their importance and how they can be used to protect our data.
Authentication protocols are a fundamental part of any system’s security, and it is essential that we understand them in order to ensure the safety of our data. Authentication protocols are used to verify the identity of a user or a device before granting access to a network or system. It aims to ensure that the user has the necessary privileges to access the network or system. Authentication protocols use different methods to authenticate users and devices, such as passwords, biometric data, digital certificates, and two-factor authentication.
Authentication Protocols Types
1. Password-Based Authentication
Password-based authentication is one of the most common methods of authentication. It requires the user to enter a username and password to access a network or system. The password must be unique, and it should be changed regularly to reduce the risk of unauthorized access.
2. Biometric Authentication
There is biometric authentication is another popular authentication method. It uses a user’s physical characteristics, such as fingerprints, retinal scans, and facial recognition, to authenticate the user. Biometric authentication is more secure than password-based authentication because it is more challenging to replicate a user’s physical characteristics. Digital certificates are another form of authentication protocol. They are used to verify the identity of a user or a device by using a cryptographic key. Following are the different types of Biometric Authentications:
- Facial Recognition
- Voice Recognition
- Fingerprint Recognition
- Iris (Retina) Recognition
- Handwriting Recognition
3. Digital Certificate
Digital certificates are usually issued by a third-party authority, such as a Certificate Authority, and they can be used to authenticate a user’s identity. Two-factor authentication is a type of authentication protocol that requires two separate pieces of information to authenticate a user. This information could be a password, a biometric scan, or something else. Two-factor authentication is more secure than other authentication methods because it requires two pieces of information to authenticate a user.
4. SAML Authentication Protocol
SAML (Security Assertion Markup Language) is an XML-based open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. It is used to provide single sign-on (SSO) access to web applications and services.
There are three entities that make up the simple SAML architecture.
- Users: Users are the end users, also called ‘Clients’.
- Identity Provider: An identity provider is a system that is responsible for authenticating and authorizing users for access to applications and other resources.
- Service Provider: Service providers are responsible for verifying the identity of users and providing them with the appropriate level of access.
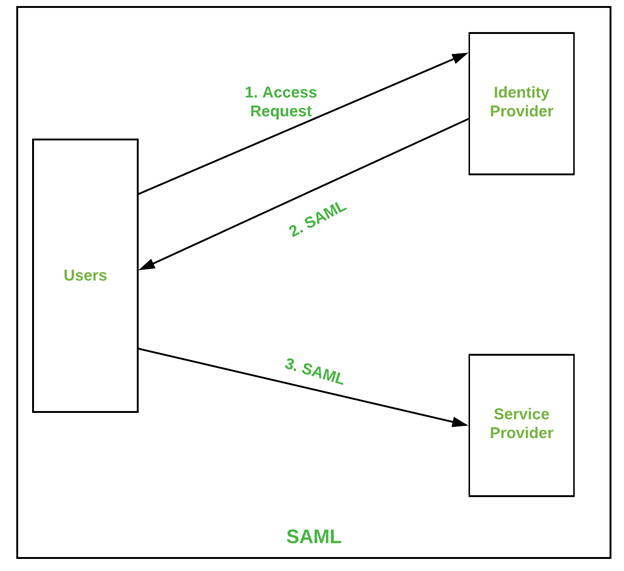
The Client sends an access request to the Identity Provider (IdP), and SAML data is shared back to the client (users). The same SAML data needs to be re-shared with the service provider to gain access to the website.
Conclusion
Authentication protocols are essential for providing secure access to networks and systems. They help to verify the identity of a user or a device before granting access, and they provide an extra layer of security by requiring multiple pieces of information to authenticate a user.
